We Help Cybersecurity Companies Create Better Buying Experiences
Innovate, differentiate, and outmaneuver the competition
GO TO MARKET STRATEGY | BUYER INSIGHTS | MESSAGING AND CONTENT | SALES ENABLEMENT
“I absolutely need a vendor who is a partner; there’s almost no exception to that need. ... security is so complex and touches so much and overlays all of the infrastructure and changes so quickly that you need a vendor who is an advisor.”
Terry Grogan, CISO Pixel Health
Transforming Vendors Into Trusted Partners
We help you build credibility and gain trust
CISO’s trust vendors who understand their problems—and can demonstrate that knowledge.
They have zero trust in vendors who rely on FUD and breach shaming to get their attention and zero tolerance for "next-generation" babble, complete solution" panaceas, and generic mind-numbing demos. They want trustworthy guidance based on relevant and credible information.
Gaining trust requires a personalized and problem-focused approach, that demonstrates an understanding of their people, processes, and technology. As well as their goals, obstacles, alternatives, and risks.
We deliver insights to pinpoint your best-fit buyers: their attributes, jobs to be done, buying triggers, and objections; and craft innovative strategies that reflect your unique business identity and value proposition.
Let us help you become a trusted advisor
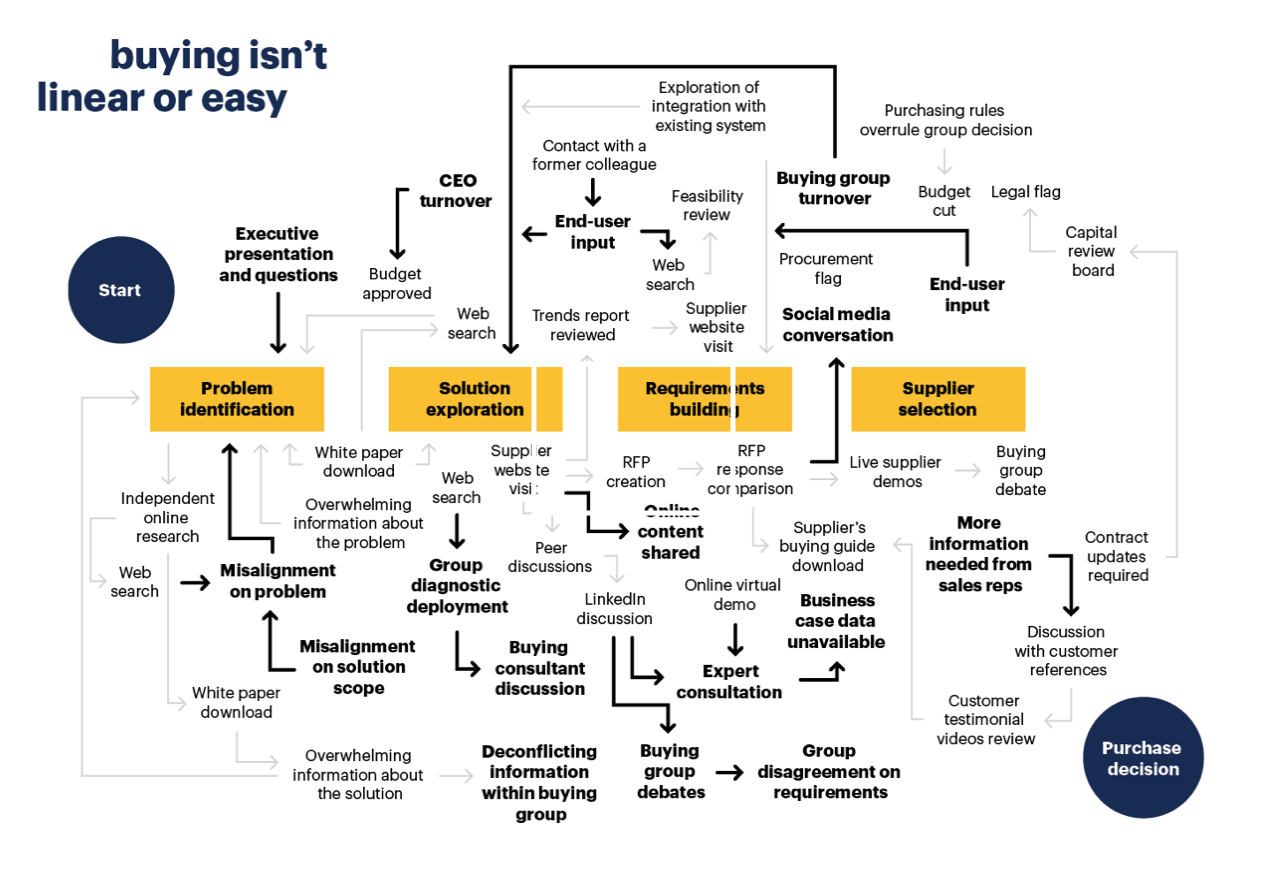
A DDoS Attack on Growth
The buying environment is a Distributed-Denial-of-Sales, so complex and exhausting it often results in no-decision.
The tsunami of incoming messages, meeting requests, and irrelevant, generic, content, demos, and presentations to the buying team force it to slow down or even crash and shut down, thereby denying sales to qualified vendors.
The opportunity for vendors who proactively guide buying teams through purchase decisions with information tailored to their needs is huge.
Our approach builds trust and results in a simpler more relevant buying experience because it's focused on the buyer and aligns sales and marketing from awareness to revenue.
"The organizations that will succeed going forward will be those that materially simplify the purchase process for customers. It’s on marketing and sales teams to take the customer by the hand and guide them through the purchase, from start to end. "Gartner
2,800 Vendors, 6,000 Products,150 Categories
A Tsunami of Technology Options and Information
Security Buyers (and Sellers) Need Guidance
Proven CyberSec Tech Chops
From the Chip to The Cloud
We're marketing pioneers who've been in the cyber ecosystem since the turn of the century- we get your tech and have the vision to position you for success
Silicon IP| DevSecOps |SasS | IoT | Embedded | Application Testing | Managed Services | Network Security | Mobile Security | Developer Tool kits | Anti-Phishing | Identity Management | IDS/IPS| Encryption | Endpoint | SaaS
|SoC |PaaS| Anamoly Detection | XDR | Biometrics |GRC.....
The technical breadth and depth to credibly translate your tech value in easy to understand language to stand out from the crowd
Experience Matters!
LEVERAGE OUR DECADES OF EXPERIENCE
We've brought to market dozens of products across the security ecosystem
Cybersecurity is more than a technology problem - it's a complex web of people, processes, and technology. We'll connect the dots between the customer's problems and environment, your offering, and the competition to craft a winning strategy that engages buyers, addresses barriers to adoption, and de-risks purchases.
We're not intimidated by complexity: be it APIs, protocols, or the algorithms that power intelligent solutions, the alphabet soup of compliance requirements and security frameworks, or processes for the SOC or SDLC. And we understand the many roles, challenges, and competing demands of the people responsible for protecting their organizations against well-funded and sophisticated attackers.
We know that in the rapidly evolving threatscape and multi-dimensional ecosystem of competitive and complementary products that opportunities to create new market categories, enter new markets, and create partnerships can appear suddenly, then slip away just as fast.
Innovative strategy defies plug ‘n play models and requires a laser focus on the customer's problems-not the product. As well as lots of experience marketing and selling on the front lines, creative, problem-solving skills, and focused thought. We take the time to assess and think deeply about each client’s unique position. Finding new opportunities, previously hidden angles, and alternatives is our specialty.
And Experience Delivers Results
As an early-stage company, we faced the challenge of having a robust technology that could be applied to a broad set of use cases across several industries. Mark’s technical depth and extensive experience allowed him to quickly grasp our technology and rapidly identify its core differentiators against a multitude of security offerings in the market.
He identified several high potential market segments. ran micro-campaigns to test and validate them -and generated over 2400 leads.
His work laid the foundation for our Marketing organization and established our go-to-market strategy. His no-nonsense, objective and methodical approach helped us focus our efforts and maximize our limited resources to accelerate our rapid growth."

"APMG played a significant role in our growth and positioned us for a successful exit by acquisition.
We worked with Mark and his team for over 2 years and they were instrumental in our turnaround. They developed our go-to-market strategy, repositioned us to enter new markets, overhauled our messaging and website, implemented Inbound marketing, and worked closely with our sales teams to drive these changes.
I’ve come to regard Mark as a trusted advisor and highly recommend the work of Agile Product Marketing Group"

"Mark's outside perspective was invaluable as he brought together company leadership in a series of workshops that pushed us to move from a product focus to a problem/solution focus centered on our customer's challenges.
He helped us zero in on our target customer profile and key differentiators, and developed new messaging to re-position the company, update our sales process, and website.
...And he’s a great guy to work with!"

A Few Of Our Clients




.gif?width=777&height=219&name=PRQA%20LOGO%204C%20(CMYK).gif)




We Collaborate with Seed-Stage Founders and Industry Leaders
STARTUPS | SCALE UPS| PIVOTS | TURNAROUNDS| M&A INTEGRATIONS

